Network Security
1. Security Planning and Design Scheme
1.1 Background
With the maturity of cloud computing technology, cloud computing service models are increasingly favored by users such as governments and enterprises due to their significant advantages. Various industries are gradually migrating more of their business applications from traditional IT architectures to cloud architectures, enjoying the convenience brought by cloud computing. However, this new service model of cloud computing also introduces changes to the traditional security protection methods.
Security is a key attribute of cloud computing and a major concern for users. Ensuring the security of cloud-based business operations is the core objective. Centered around the three pillars of information security—confidentiality, integrity, and availability—and based on the concept of in-depth defense, this plan divides the data center into multiple security zones according to business functions and network security risks. It implements both physical and logical control measures to achieve isolation, enhancing the network's capability for self-protection, fault tolerance, and recovery in the face of intrusions and insider threats. The goal is to design an overall cloud security solution.
This plan aims to comprehensively assess the current security status of the existing information systems, identify potential security risks, and establish practical security measures to build a sound and sustainable information security management system. Meanwhile, this plan will also ensure that the company complies with relevant international laws and regulations in terms of compliance. This will enable the company to effectively respond to various information security threats while staying within the bounds of legal and regulatory compliance.
1.2 Business System Architecture
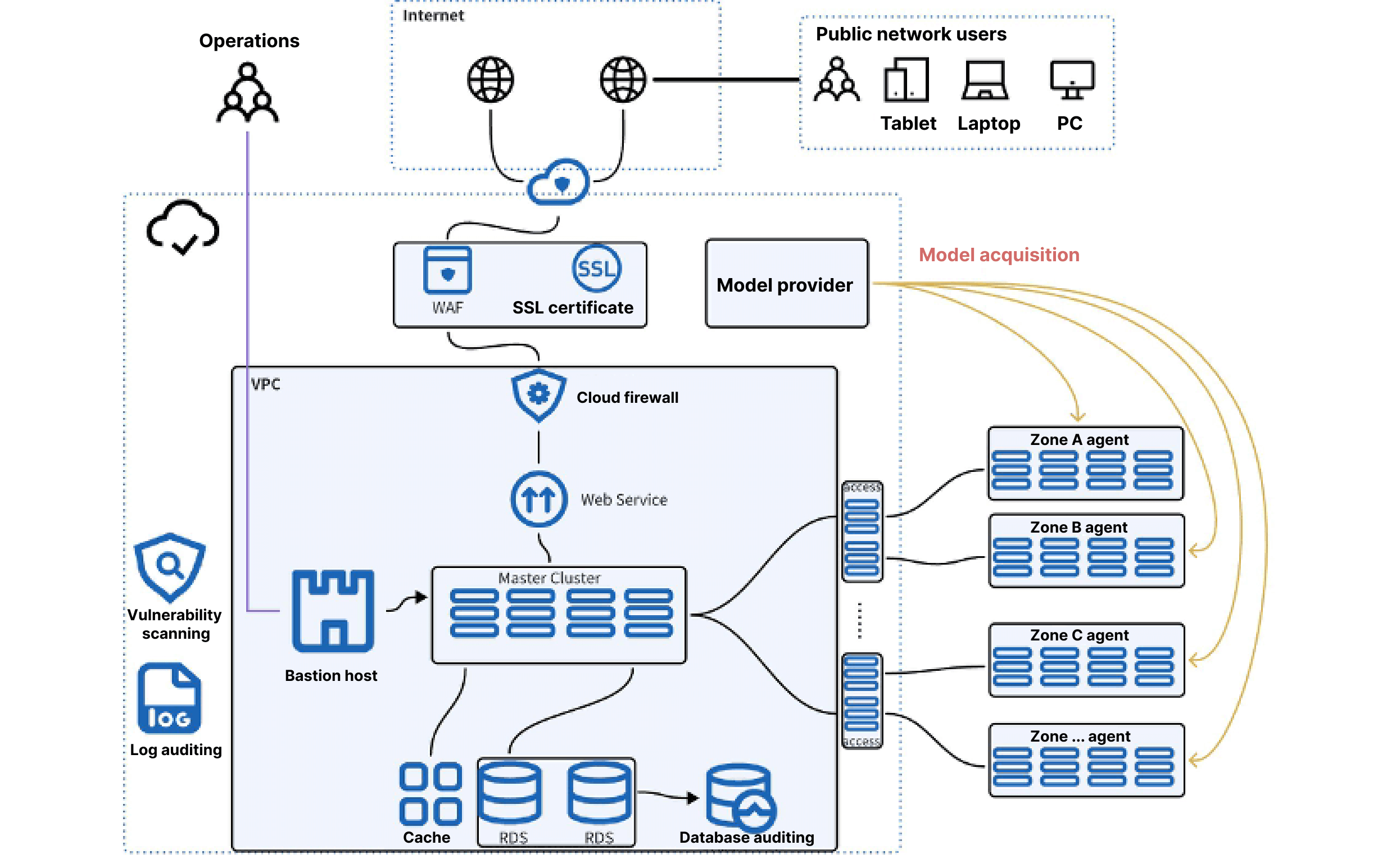
The components and communication relationships involved in this business system are as follows:
○ Agent
▪ Functions:
● Responsible for managing the GPU in the host operating system and executing GPU scheduling based on instructions from upper layers.
● Reports business status and management status to the Access node.
▪ Communication
● Access: Internet communication
○ Access
▪ Functions:
● Receives reported information from the Agent component.
● Aggregates information from its zone and reports it to the Master.
● Receives instructions from the Master and distributes them to the Agent.
▪ Communication
● Master: Internet communication
● Agent: Internet communication
○ Master
▪ Functions:
● Receives instructions from Web Service and distributes them to subordinate Access nodes.
● Receives data reported by Access, analyzes, aggregates, and stores it in the database.
▪ Communication
● Access: Internet communication
● Web Service: VPC communication
○ Web Service
▪ Functions:
● Provides an HTTP operation interface for end users.
● Provides HTTP API services for end users.
● Converts end-user commands into internal system instructions and distributes them to the Master.
▪ Communication
● Master: VPC communication
● End Users: Internet communication
1.3 Overall Security Plan
This plan addresses the exposure of the business system to the internet by implementing security components at each layer. The details are as follows:
1. Communication Security
● Within the system:
○ Communication between agent, access, master, and web service must be encrypted with the following requirements:
■ TLS 1.2 or above
■ Encryption key of 2048 bits
● For end users:
○ Services must be provided over HTTPS.
○ Encryption system requirements are the same as for internal system communication.
2. Perimeter Security
● Web Service:
○ First line of defense: Use a proxy-based anti-DDoS service
■ Purpose:
● To defend against layer 3/4 DDoS attacks from the internet.
■ Configuration Considerations:
● Provide a defense IP to end users for anti-DDoS service.
● Configure the source of the anti-DDoS service to point to the WAF defense IP.
○ Second line of defense: Use a WAF (Web Application Firewall) service
■ Purpose:
● To defend against various HTTP-level attacks from the internet.
■ Configuration Considerations:
● Configure the WAF source to point to the real address of the web service.
○ Third line of defense: Network firewall
■ Purpose:
● Effectively isolate internal and external network attacks.
● Restrict access from external networks, reduce unnecessary network exposure, and lower potential security risks.
■ Configuration Considerations:
● Only allow end users to access port 443 of the Web Server.
● Access:
○ ACL (Access Control List) control:
■ Purpose:
● Only allow access to the communication ports used by Master and Agent.
■ Configuration Considerations:
● Only allow access to the communication ports used by Master and Agent.
● Master:
○ Network firewall:
■ Purpose:
● Effectively isolate internal and external network attacks.
● Restrict access from external networks, reduce unnecessary network exposure, and lower potential security risks.
■ Configuration Considerations:
● Only allow traffic from the external network to access the service ports provided by Master for Access.
● Agent:
○ ACL control:
■ Purpose:
● Only allow access to the communication ports used for Access.
■ Configuration Considerations:
● Only allow access to the communication ports used for Access.
3. Host Security
● All system components involved:
○ HIDS (Host-based Intrusion Detection System):
■ Purpose:
● Provides intrusion detection and protection against viruses and malware.
○ System hardening:
■ Configure firewall:
● Enable firewall and set rules to limit access to the system and block unauthorized network traffic.
■ Strengthen account and password policies:
● Use complex passwords, change passwords regularly, restrict account access, and disable unnecessary default accounts.
■ Disable unnecessary services.
■ Enable audit logging processes.
■ Configure ACL based on business needs.
4. Operational Security
● Web Service, Access, Master:
○ Bastion host:
■ Purpose:
● The bastion host serves as a unified entry point for operations. Operations personnel are prohibited from directly logging into system components from the public network.
● Prevent malicious attackers from directly accessing internal network resources. This isolation reduces the risk of direct attacks on internal servers.
■ Notes:
● Use internal network IPs for SSH and other management operations whenever possible.
5. Data Security
● Various types of databases used within the system:
○ Database audit system:
■ Purpose:
● Ensure the security, compliance, and integrity of the database system.
6. Auditing
● Web Service, Master:
○ Log auditing system:
■ Purpose:
● Used for compliance auditing and identifying potential security threats and abnormal behavior.
7. Risk Management and Detection
● Vulnerability scanning:
○ Purpose:
■ Scan system services and host assets exposed to the internet to detect security vulnerabilities in the system and applications and assess the security posture.
1.4 Security Service List
This solution is designed with a comprehensive and in-depth defense strategy based on a thorough understanding of hacker attack methods and approaches. It ensures the security of the cloud platform and covers host security, edge security, application security, data security, and security management.
Based on the layered and in-depth security defense system, the plan includes specialized security products and technologies covering different security categories:
| No. | Product & Service | Function Overview | Category |
|---|---|---|---|
| 1 | Anti-DDoS | Protects against TCP, UDP, and ICMP Flood attacks. | Edge Security |
| 2 | Cloud Firewall | Isolates the secure internal network from the insecure external network, preventing viruses or attacks from entering the internal network. Enhances security policies, limits exposed user endpoints, etc. | Edge Security |
| 3 | Web Application Firewall (WAF) | Conducts comprehensive detection and protection for website traffic, effectively defending against various common web attacks and intrusions. Reduces website security risks. | Application Security |
| 4 | Bastion Host | Manages cloud host operations, including account management, permission control, authorization, audit records, etc. | Security Management |
| 5 | Vulnerability Scanning | Detects weaknesses by simulating attack vectors that hackers might exploit, helping organizations prevent data breaches, malicious intrusions, and other security threats. | Security Management |
| 6 | Log Auditing | Regularly collects, analyzes, stores, and monitors operation logs generated by computer systems, network devices, applications, and other IT infrastructure. | Security Management |
| 7 | Database Auditing | Intelligently analyzes database communication traffic, providing fine-grained auditing of database access behaviors. Enables real-time alerts for dangerous attacks, intelligent warnings for risky statements, and ensures the security of sensitive database assets through comprehensive auditing. | Security Management |
| 8 | SSL Certificate | Provides identity verification, access control, integrity of information, confidentiality of critical data transmission, storage, and ensures non-repudiation of data origin and receipt. | Communication Security |
| 9 | HIDS (Host-based Intrusion Detection System) | Monitors cloud host security in real time, quickly detecting hacker intrusions and helping users understand and harden the security of their servers. | Host Security |
2. Security Service Function Description
An efficient, multi-dimensional, full-stack protection system also includes various edge defense measures. By strategically deploying security functions at network boundaries and within the trust boundaries between internal network zones, it effectively achieves edge security protection.
Beyond ensuring edge security, this plan also utilizes products like vulnerability scanning, log auditing, and bastion hosts to create a comprehensive and efficient information security management system. This system protects organizations from both internal and external threats, ensuring the safe and stable operation of data and business systems.
2.1 DDoS Attack Protection
The DDoS protection service offers managed DDoS protection through a detection and intelligent defense system. It automatically and swiftly mitigates network attacks, reducing business disruption such as increased latency, restricted access, and service outages, thereby minimizing business losses and the risks of potential DDoS attacks. This ensures business operations remain unaffected by Distributed Denial of Service (DDoS) attacks, maintaining service continuity and stability. The deployment not only addresses basic protection needs but also delves into business specifics, allowing for customized security strategies that adapt to diverse application scenarios.
Key aspects include:
● In-depth Business Understanding: A comprehensive analysis of the business is conducted to identify key business modules, applications, and service layers that need prioritized protection. This involves understanding unique traffic characteristics and resource consumption patterns.
● Multi-dimensional Risk Assessment: Based on historical data analysis, industry case studies, and the latest threat intelligence, a comprehensive evaluation of potential DDoS attack models is conducted, including but not limited to SYN Flood, UDP Flood, and HTTP Flood. Additionally, factors such as attack scale, complexity, and evolving trends are considered to identify weak points and potential risks within the system.
● Advanced Functional and Intelligent Requirements: In addition to basic traffic cleansing, the solution offers deep packet inspection (DPI) technology for enhanced application-layer protection. It also supports machine learning algorithms to automatically learn and identify normal and abnormal traffic patterns while providing intelligent policy optimization to dynamically adjust defense strategies based on real-time traffic.
● Customized Strategy Refinement: Tailored traffic threshold settings are implemented based on specific business applications, allowing for differentiated protection strategies for web services, database access, VoIP communication, and more.
● Intelligent Monitoring and Visualization Management: The system integrates advanced monitoring capabilities, tracking network traffic dynamics, device status, and potential attack activities in real-time. It also provides an intuitive graphical interface, enabling security teams to quickly identify and address issues.
Through these detailed and comprehensive deployment and management strategies, the business will establish an impenetrable security defense, effectively countering increasingly complex DDoS attacks and providing a solid foundation for stable business operations and sustained growth.
2.2 Network Firewall
The network firewall plays a critical role in modern network security systems, acting as a strong barrier that separates the secure internal network from the potentially threatening external network. Here is an extended description of this function:
The primary function of a network firewall is to isolate the internal network from the external network. The internal network typically refers to the internal environment of an enterprise or organization, containing sensitive data and critical business applications. The external network, on the other hand, is an open environment filled with unknown and potential dangers such as viruses, malware, and malicious attacks. By precisely controlling the data flow between the internal and external networks, the firewall effectively blocks external threats from entering the internal network, ensuring the safety of internal data.
The firewall also strengthens security policies by limiting exposed user endpoints. It enforces various security policies that reduce the risk of attacks on the internal network and enhance overall security. Additionally, the firewall restricts access to the external network, reducing unnecessary exposure points and lowering potential security risks.
2.3 Web Security Protection
Deploying a Web Application Firewall (WAF) is a crucial defense measure against web application layer attacks. A WAF provides comprehensive defense against various web application layer security threats.
● DDoS Attack Mitigation: WAF effectively counters web application layer DDoS attacks like HTTP/HTTPS flood attacks and slow connection attacks through traffic monitoring, anomaly detection, and automated mitigation. WAF intelligently analyzes traffic, swiftly identifying and blocking malicious traffic to protect web applications from disruptions.
● SQL Injection and Cross-Site Scripting (XSS) Prevention: WAF deeply inspects HTTP requests and responses, detecting and blocking malicious SQL statements or script code to safeguard web applications from these common vulnerabilities.
● Cross-Site Request Forgery (CSRF) Defense: WAF detects abnormal client requests and dynamically defends based on access control policies, preventing legitimate user operations from being maliciously exploited.
● Component Vulnerability Protection: WAF updates protection rules based on well-known vulnerability databases, automatically detecting and blocking attacks that exploit third-party component vulnerabilities, adding essential security protection for web applications.
● Identity Forgery Threat Mitigation: WAF, combined with authentication mechanisms, analyzes request sources and user behavior characteristics to effectively detect and prevent illegal logins, account hijacking, and other identity-related attacks.
In summary, deploying a WAF is key to protecting externally-facing web applications from various web attacks. A WAF comprehensively monitors and defends against web application layer security threats, including DDoS attacks, SQL injections, XSS, CSRF, component exploitation, and identity forgery, providing robust security protection for web systems.
2.4 Vulnerability Scanning
A vulnerability scanning system is an automated network security tool designed to identify security flaws in computer networks, systems, applications, and web services. These systems simulate attack vectors that hackers might exploit to detect weaknesses, helping organizations prevent data breaches, malicious intrusions, and other security threats.
Key features include:
● Multi-Engine Technology: Integrates multiple leading scanning engines, including both commercial and open-source tools, leveraging their combined strengths for deep scanning across systems such as operating systems, middleware, databases, network devices, and applications.
● Intelligent Scan Scheduling: Dynamically adjusts scan priorities and frequencies based on network topology, system importance, and historical scan results, minimizing business disruption and improving scan efficiency.
● Comprehensive Coverage: Regularly performs full network scans, covering internal networks, cloud assets, containers, and IoT devices, ensuring no areas are overlooked. Agent technology is used for in-depth scanning of hard-to-reach internal systems.
● Risk-Based Categorization: Vulnerabilities are classified based on CVE scores, CVSS standards, and custom rules, allowing rapid identification of high-risk vulnerabilities.
● Automated Impact Analysis: Evaluates the potential impact of vulnerabilities on business operations by considering asset importance, business relevance, and exploitability, generating detailed impact reports.
● Automated Remediation Guidance: Generates detailed remediation guides for each identified vulnerability, including applicable patch information, temporary mitigation measures, and best practice recommendations.
● Repair Verification and Rollback Strategies: After implementing fixes, the system automatically verifies that vulnerabilities have been properly resolved and prepares rollback plans to address any unintended issues.
● Visualization of Repair Progress: A dashboard tracks key metrics like vulnerability distribution, repair progress, and overdue patches, supporting management decision-making.
● Periodic Review Mechanisms: Conducts periodic reviews of fixed vulnerabilities to ensure long-term effectiveness, preventing reintroduction due to new versions or configuration changes.
● Automated Reporting and Compliance Checks: Generates regular vulnerability reports to meet internal audit and industry compliance requirements, such as PCI-DSS and HIPAA.
● Customized Scan Rules: Customizes scanning rules based on the organization’s unique security policies and historical incidents, enhancing the ability to detect specific threats.
● Machine Learning Assistance: Uses machine learning models to analyze historical scan data, automatically optimizing scanning strategies, improving detection of unknown threats, and reducing false positives and false negatives.
This comprehensive approach not only significantly enhances vulnerability management efficiency and effectiveness but also improves the organization’s security posture, providing a solid foundation to address increasingly complex security challenges.
2.5 Log Auditing
Log auditing is a systematic security practice that involves the regular collection, analysis, storage, and monitoring of operation logs generated by computer systems, network devices, applications, and other IT infrastructure. This process is essential for identifying potential security threats, abnormal behavior, compliance issues, and system performance bottlenecks.
Objectives:
● Security Monitoring: Analyze log data to quickly detect unauthorized access attempts, malicious activities, and internal misuse.
● Compliance: Ensure data processing activities are traceable and auditable to meet industry standards and regulations such as SOX, PCI-DSS, GDPR, etc.
● Fault Diagnosis: Help technical teams quickly locate the causes of system failures and performance issues.
● Operational Auditing: Record and review user and administrator actions to ensure compliance and provide evidence for incident investigations.
Core Features:
● Information Collection: Automatically gather log data from various sources, including system logs, application logs, and security event logs.
● Information Analysis: Use algorithms and rule engines to automatically analyze log data, identifying abnormal patterns and potential threats.
● Information Storage: Securely store log data, ensuring its integrity and long-term accessibility.
● Information Display: Provide intuitive interfaces or reports to display log analysis results, making it easier for security personnel to understand and respond.
● Alarm Response: Automatically trigger alerts for critical incidents and provide predefined response measures.
Technical Implementation:
● Automation and Intelligence: Leverage machine learning and AI to enhance the accuracy of log analysis and automatically detect abnormal behavior.
● Log Standardization: Convert logs of different formats into a unified standard format for consistent management and analysis.
Best Practices:
● Regular Audits: Set up a regular audit schedule to make log reviews a routine process.
● Permission Control: Restrict access to log data to authorized personnel only, ensuring data confidentiality.
● Data Protection: Encrypt sensitive log data to prevent unauthorized access.
● Log Retention Policy: Define retention periods and deletion rules for log data based on regulatory requirements and business needs.
Log auditing is a crucial component of an Information Security Management System (ISMS). It not only helps organizations quickly identify and respond to security threats but also provides key evidence for post-incident investigations, forming the foundation for maintaining cybersecurity and regulatory compliance.
2.6 Communication Security
The HTTP protocol does not encrypt data, which can lead to risks like data leakage, tampering, or phishing attacks during transmission. Deploying SSL certificates (Secure Sockets Layer certificates, now commonly referred to as TLS, or Transport Layer Security certificates) is crucial for modern web applications. The importance of SSL/TLS certificates can be summarized as follows:
Protecting User Data Security:
SSL certificates encrypt the data transmitted between users and servers, ensuring that sensitive information (like credit card numbers, passwords, and personal identity data) cannot be intercepted or altered during transmission. This is a key defense against data breaches and man-in-the-middle (MITM) attacks.
Building Trust:
SSL certificates are issued by trusted Certificate Authorities (CAs) following rigorous validation processes. When users visit a website with a valid SSL certificate, their browser displays a padlock symbol and the "HTTPS" prefix, enhancing trust in the website. This trust is particularly crucial for e-commerce sites, banks, and financial service platforms handling large volumes of sensitive information.
Improving Search Engine Rankings:
Since 2014, search engines like Google have started using HTTPS as a ranking factor. Websites with SSL certificates may rank higher in search results, thereby increasing visibility and attracting more traffic.
Compliance with Regulatory Requirements:
As cybersecurity regulations become stricter, many countries and regions now mandate that organizations handling personal data or offering electronic services must use HTTPS to secure user data. For instance, the European GDPR (General Data Protection Regulation) has specific requirements for the security of data processing.
Preventing Phishing Attacks:
SSL certificates also help prevent phishing attacks by verifying the identity of websites. By confirming domain ownership, SSL certificates ensure that users are connecting to the legitimate site and not a malicious imitation.
Enhancing Brand Image:
Websites using SSL certificates and displaying the HTTPS prefix are generally perceived as more professional, trustworthy, and reliable. This improves brand reputation and helps attract more users and customers. In summary, deploying SSL certificates is essential for securing user data, building trust, improving search engine rankings, complying with regulations, preventing phishing attacks, and enhancing brand image. Therefore, implementing SSL certificates is a necessity for any organization that aims to operate securely on the internet and gain user trust.